Ok, this isn’t a hack. It’s more of a tip that may help you protect data. Some of you would not have clicked a link to Andy’s Database Credentials Tip. You are welcome.
LastPass
I like LastPass. I pay for Premium and it’s not a bad deal, in my humble opinion.
I also like Azure – a lot. As a Microsoft Data Platform MVP, I get a free subscription to Azure. But there was a time when I paid for my Azure subscription. It was worth it, in my humble opinion.
Provisioning an Azure SQL DB
When it’s time to provision an Azure SQL DB, I sometimes configure a username and password. (You can also use Azure Active Directory to connect to an Azure SQL DB instance).
Back in the day, I would use some generic – but easy to guess – name for the Administrator account. Something like “andy,” for example.
The LastPass Chrome extension includes a Generate Secure Password option:
I use this to generate the Server Admin Login value:
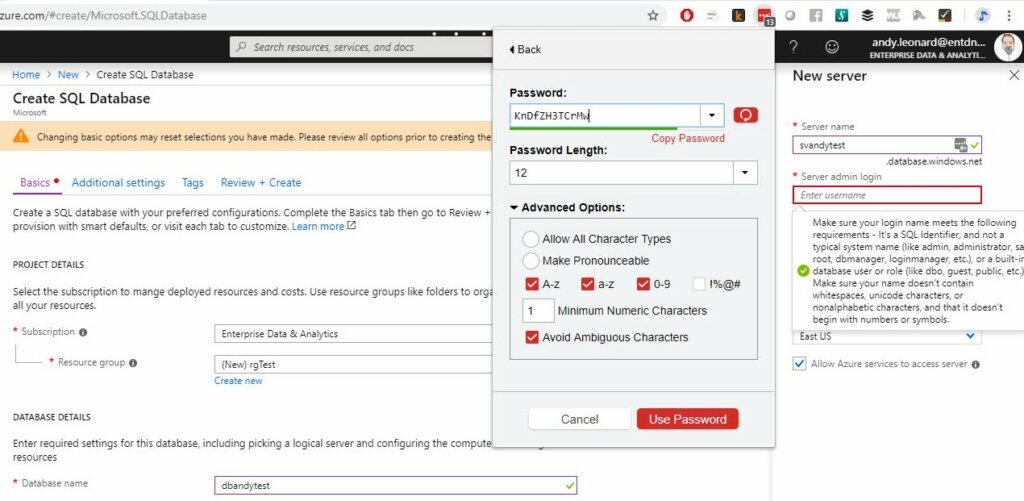
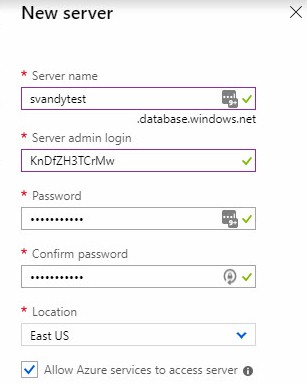
My thinking? Why give away half the key-value pair for logins?
Conclusion
LastPass isn’t the only way to generate a random string. I leverage it because, well, it’s right there in my browser already.
I cannot provide metrics for how often this trick has thwarted would-be attacks. I also do not know if this even slows bad guys down these days. But I’ve been doing this for a while and – if nothing else – it gives me a little peace of mind.
:{>



One thought on “Andy’s Database Credentials Hack”