
Visit the landing page for the Data Engineering Execution Orchestration Frameworks in Fabric Data Factory Series to learn more.
I must begin this post with a simple – perhaps profound – statement: Koen Verbeeck (LinkedIn | @Ko_Ver) is a talented data engineer. Here’s why I begin this post with such a statement.
Koen’s Great Idea
Koen found – and blogged about – a way to configure Azure security to work with the Fabric Data Factory ReST API! With his permission, I base this post on Koen’s work (thanks Koen!).
My Version of Koen’s Great Idea
The problem we are trying to solve is: Grant an Azure Data Factory permission to execute the ReST API method calls against artifacts in a Fabric workspace.
I begin visiting the Azure Portal. If you don’t have an Azure account, you can create one. You can do a lot of things in Azure for little money, but you need an account and that account needs to be secured by a working source of funds in case you leave a virtual machine running for days. Hypothetically. BE CAREFUL. DO NOT LEAVE A VM RUNNING FOR DAYS.
First, You Need an Azure Data Factory
If you’re following along at home, search for “data factories” and then click on “Data factories”:
Once the Data Factories blade displays, click the “Create” button to begin creating a shiny new Azure Data Factory:
I create mine in a new Resource Group named rgguf and I name the data factory dfguf:
If you’re lazy efficient – like me – you can accept the other settings on the Create Data Factory page and just click the “Review + create” button. When you reach the next page, you can click the “Create” button:
In a matter of minutes, your data factory will be ready. Click the Go to resource button to, well, go to the resource group page:
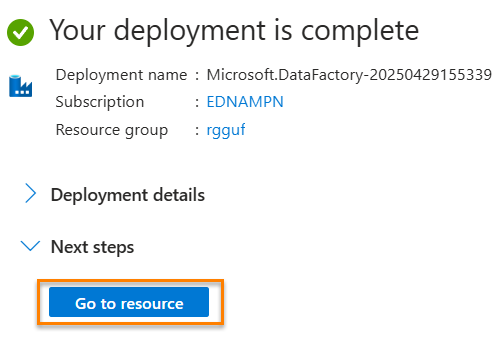
Click the data factory to visit the data factory page:
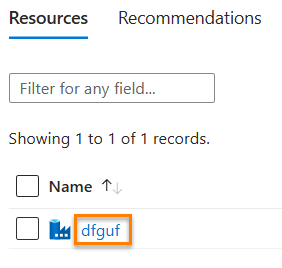
Here, we’re about to create a Microsoft Entra ID Group that contains a single member: the Azure Data Factory SAMI (System-Assigned managed Identity). Later, we’re going to add the Azure Data Factory SAMI as a Contributor to a Fabric Workspace.
So… why this extra step? Why not just add the ADF SAMI directly in the Fabric workspace?
As Koen points out:
In Azure, Setup Microsoft Entra Security
We next need to configure an Azure Active Directory… er, I mean, a Microsoft Entra ID group to proceed.
Fabric It’s easy enough to locate Microsoft Entra ID in the Azure portal, simply type “Azure Active Directory” in the search box and the first result will usually be “Microsoft Entra ID”:
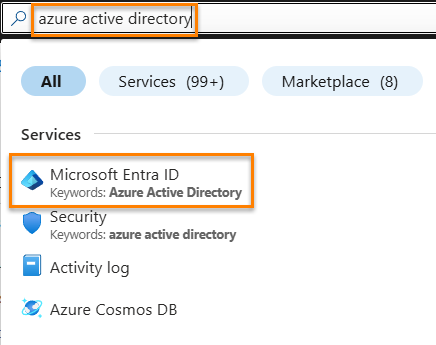
Click Groups:
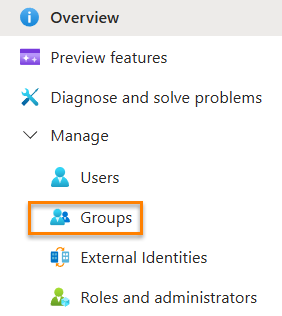
Click New group:
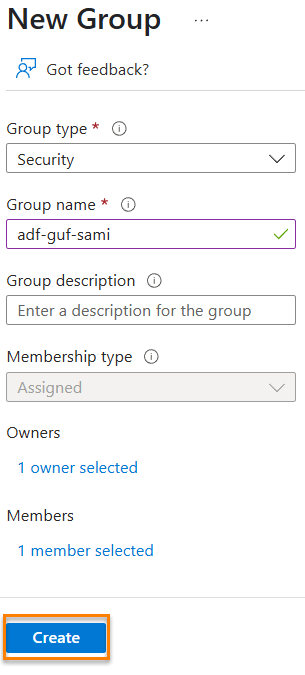
Configure the new group thus:
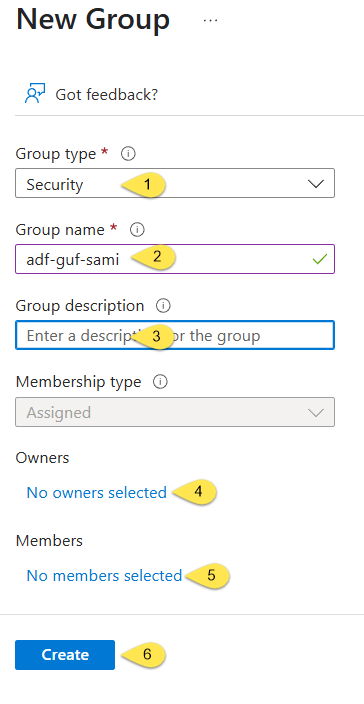
- Confirm the Group type is set to “Security”
- Enter a memorable group name (like adf-guf-sami)
- Optionally, enter a description for the new group
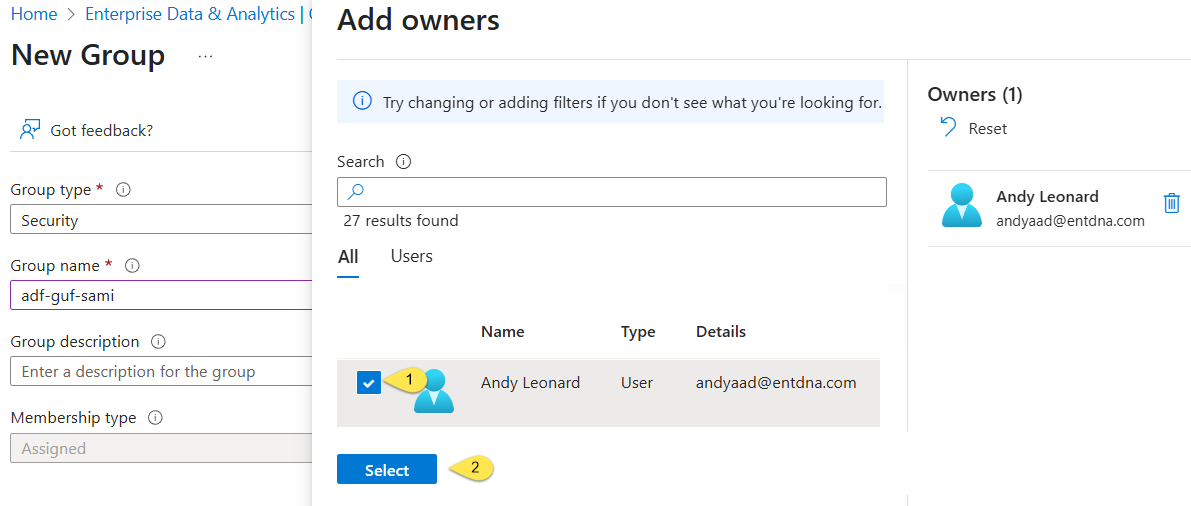
- Click the “no owners selected” link and pick an owner. I recommend picking yourself. If you don’t already have a Microsoft Entra ID account configured for yourself (or for anyone), this article will help you get started:
- Next, click the “No members select” link. You can search for your data factory – like I did here – and then select it:
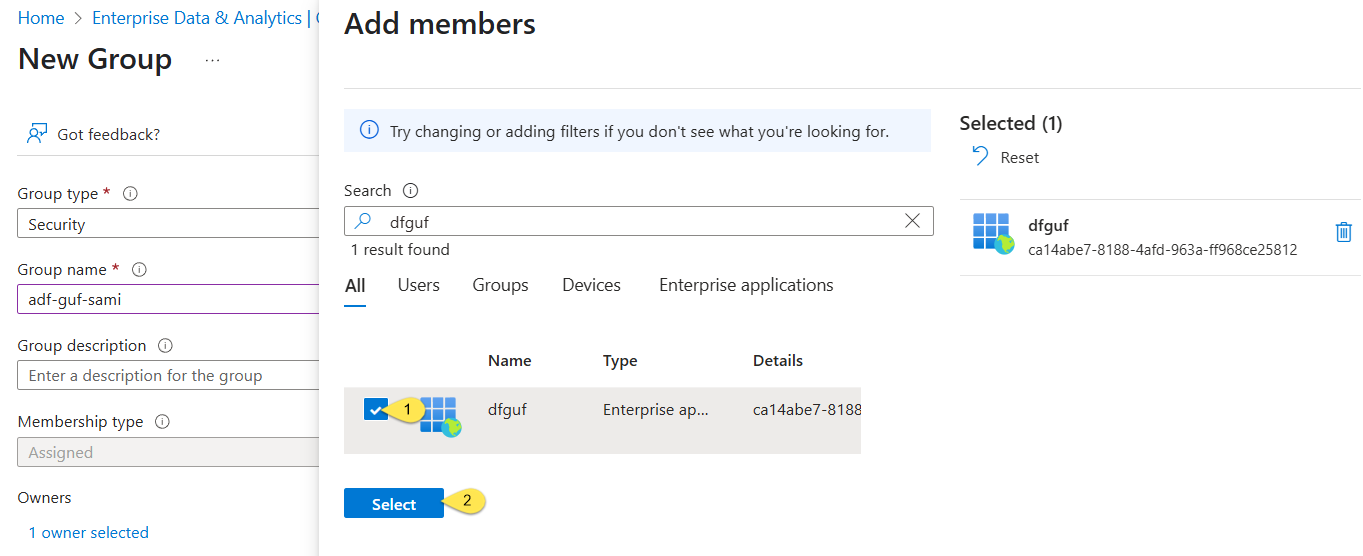
- Click the Create button and you’re off to the races!
In Fabric, Enable API Security for Your Microsoft Entra ID Group
Visit the Fabric portal (application?). If you don’t have a Fabric configured, you can create a free trial (at the time of this writing). You will need an email address that exists within a Microsoft365 tenant, a personal email address will not do.
Click the Fabric settings gear:
Click “Admin portal”:
Search for API, and then scroll until you find Developer settings and click on “Service principals can use Fabric APIs”:
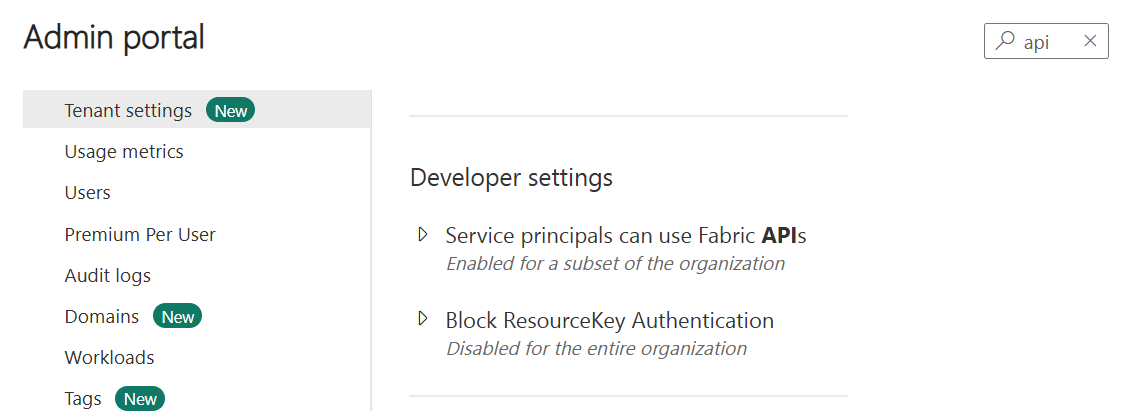
When “Service principals can use Fabric APIs” displays:
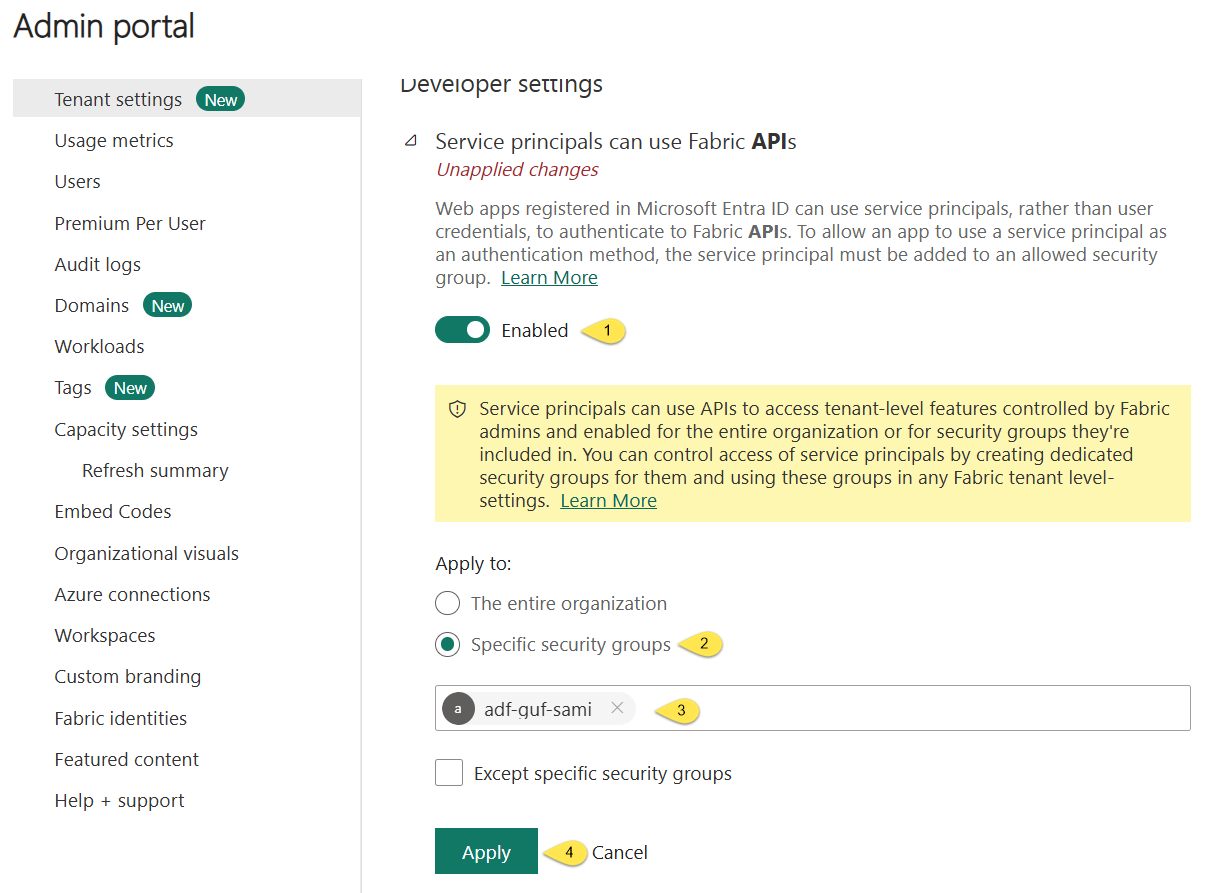
- Enable “Service principals can use Fabric APIs”
- Select “Specific security groups” under “Apply to”
- Enter your Microsoft Entra ID group name into the text box
- Click the Apply button
In Fabric, Setup a Workspace + Security
Next, click Workspaces:

Click the new workspace button:
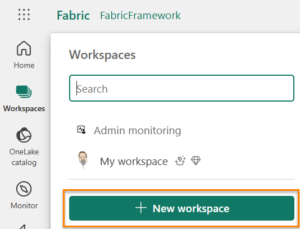
- Name your new shiny workspace (I named mine… you guessed it: wsguf):
- Click the Apply button:
Click Manage access:
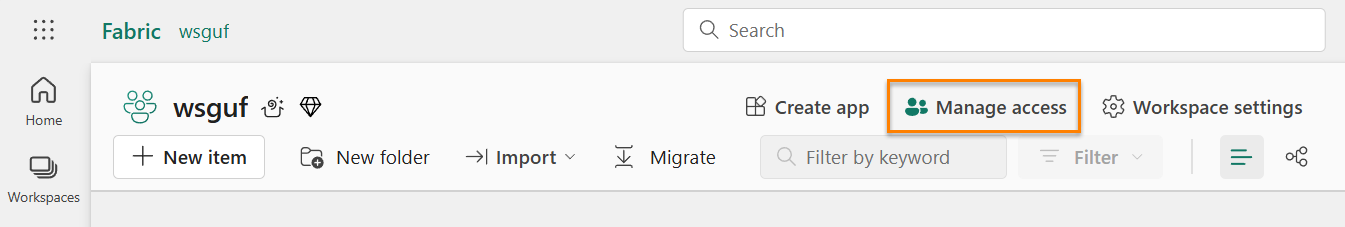
When the “Manage access” blade displays, click the “+ Add people or groups” button:
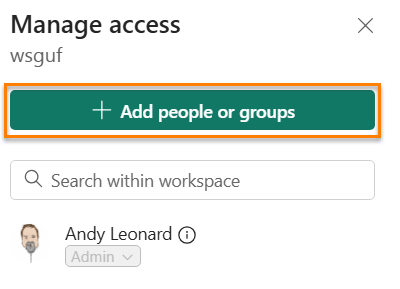
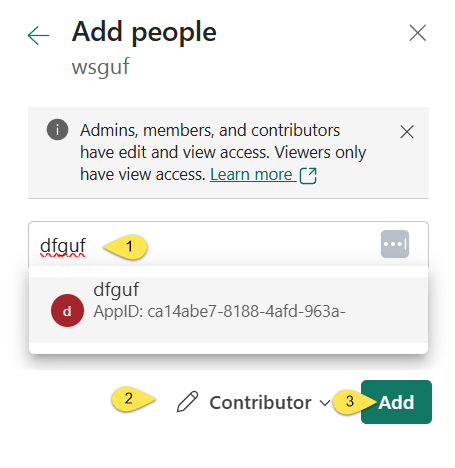
When the “Add people” blade displays
- Enter the name of the Azure Data Factory
- Change the role to “Contributor”
- Click the “Add” button:
The Azure Data Factory SAMI now has Contributor access to the Fabric workspace:
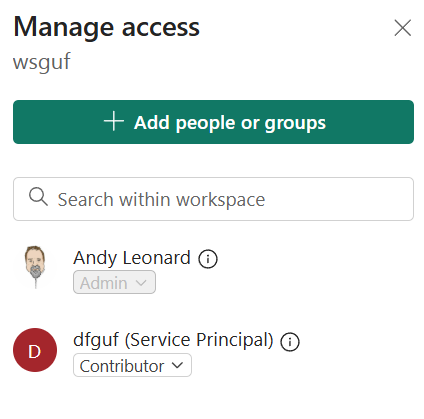
Conclusion
The Azure Data Factory now has permission to execute the ReST API against artifacts in the Fabric workspace.
Need Help?
Consulting & Services
Enterprise Data & Analytics delivers data engineering consulting, Data Architecture Strategy Reviews, and Data Engineering Code Reviews!. Let our experienced teams lead your enterprise data integration implementation. EDNA data engineers possess experience in Azure Data Factory, Fabric Data Factory, Snowflake, and SSIS. Contact us today!
Training
We deliver Fabric Data Factory training live and online. Subscribe to Premium Level to access all my recorded training – which includes recordings of previous Fabric Data Factory trainings – for a full year.
:{>



Comments